The second most common type of malware incident is the notorious ransomware attack. According to the Verizon 2020 Data Breach Investigations report, the primary aim of a ransomware attack is “to disrupt operations badly enough and long enough that the organization will pay the ransom.” The average ransom payment in Q2 2020 was a whopping $178,254 — a 60% increase from Q1.
This article explains what ransomware is, why ransomware is a uniquely tricky cybersecurity threat, and how companies can prevent, detect and respond to ransomware infections:
What Is Ransomware?
Ransomware is a type of malware that restricts the targeted user from accessing systems or data until a ransom is paid to the attacker. Hackers usually encrypt the victim’s data and withhold the decryption key until the ransom is paid.
Although attackers sometimes threaten to destroy or publish sensitive data, the most pressing concern for organizations is usually business continuity: Since data in the compromised system is encrypted, it is unavailable for users and software applications, so business processes come to a halt.
The Challenge in Detecting Ransomware
Ransomware attacks are difficult to detect quickly enough to prevent damage. Cybercriminals use crafty social engineering techniques to install ransomware and military-grade encryption algorithms to scramble sensitive data. Once a computer or other endpoint is infected, ransomware can propagate itself throughout the network and execute extremely quickly, which makes it nearly impossible to respond in time. Often, the targeted organization becomes aware of the infection only when the ransomware has encrypted its data and announced its presence to the organization to demand payment.
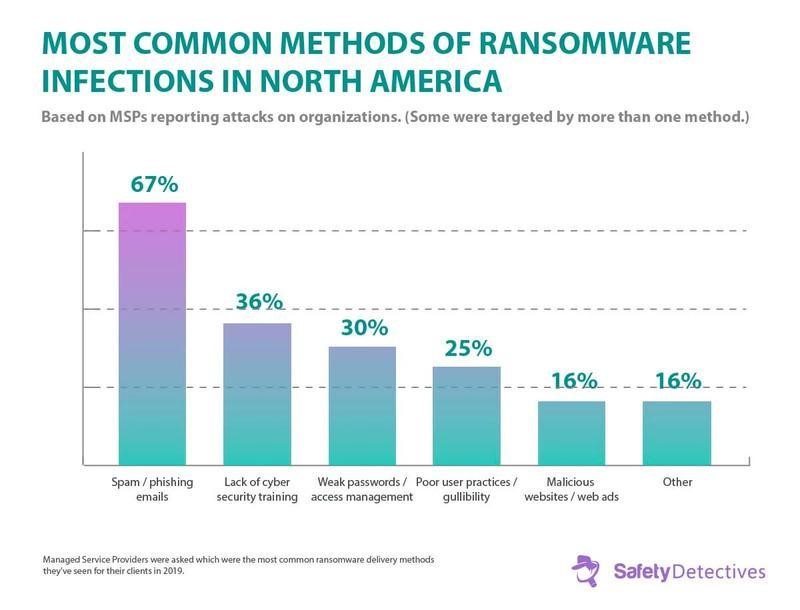
Most Common Ways to Get a Ransomware Infection
The most common ways to get infected by ransomware are:
- Spam and phishing emails — Ransomware authors often pose as legitimate users to trick others into downloading malicious Be sure you have a strong email security protection system that verifies who sent messages and checks email attachments.
- Malicious websites — Some websites host malware and phish for sensitive information such as login credentials. This method often requires user interaction, such as clicking on fake ads or social media links and entering information in fake login fields, so ensure the browsing policies in the company are set to enable safe browsing.
- Infected removable drives — USB flash drives can contain malware that automatically installs when you connect the drive to your computer. Be sure computers run security scans of removable drives and disable the autorun feature.
- Malicious applications and plug-ins — Malware authors often bundle their viruses with software shared through third-party websites. Make sure you carefully read over what you’re installing, and download software only from official websites. Also, make sure that regular users don’t have permissions to download and install software on their computers.
2020 also saw an increase in Remote Desktop Protocol intrusions, which do not require user input and are especially difficult to detect.
Common Sources of Ransomware
Types of Ransomware
The main types of ransomware to look out for are:
- Locker ransomware — This type of malware restricts access to the infected
- Crypto ransomware — Perhaps the most dangerous type of ransomware, this malware restricts access to stored data and files. It encrypts the user’s data and demands a ransom in exchange for the decryption key. However, paying the ransom doesn’t guarantee getting the key.
- Mobile ransomware — This type of malware is spread from a mobile device to a computer and typically displays a message claiming that the device has been locked due to some type of illegal activity.
Signs of a Ransomware Attack
Some indicators of a ransomware attack include:
- Anomalous file system activity, such as hundreds of failed file modifications (due to the ransomware attempting to access those files)
- Increased CPU and disk activity for no apparent reason (due to the ransomware searching for, encrypting and removing data files)
- Inability to access certain files (a result of ransomware encrypting, deleting renaming or relocating data)
- Suspicious network communications (caused by interaction between the ransomware and the attackers’ command and control server)
Best Practices for Ransomware Detection
No business is immune to cybersecurity threats, but there are several best practices that will reduce your risk of falling victim to a malware attack and enable you to spot attacks in progress.
Educate your employees
Provide employees with a list of actions to take if they come across a suspicious email or link. Teach them about red flags in malicious emails, such as:
- Corporate-looking email accounts
- Suspicious file attachments
- Suspicious links to external URLs
Monitor your systems
Monitor your systems for signs of suspicious activity:
- Scan file systems for atypical activity, such as. hundreds of failed file modifications.
- Log all incoming and outgoing traffic.
- Determine the baseline of normal user activity and proactively look for aberrations.
- Promptly investigate any unusual activity.
Create honeypots
Honeypots are decoys — fake file repositories that look like legitimate repositories. Hackers will target honeypots, enabling you to spot them. Early detection helps with safe malware removal and protects your infrastructure from being compromised. FSRM ransomware protection is an excellent example of honeypot usage.
Use software solutions
Use whitelisting software with antivirus/anti-ransomware tools that will alert you to threats.
Check email content
Check and systematically filter spam or suspicious email content:
- Configure email settings to automatically filter incoming mail and prevent suspicious messages from entering a user’s inbox.
- Disallow files with certain extensions in mail attachments, such as executable files.
Conclusion
Ransomware is a notoriously challenging form of malware to detect and protect against. But by taking necessary precautions, such as educating your employees on common red flags and vulnerabilities, establishing processes and systems for preventative monitoring, and installing anti-ransomware software and tools, organizations can effectively safeguard their systems and protect their sensitive data.


